2 min read
Your Small Business Guide to Dark Web Defense
Navigating the Cyber Battlefield in the beginning of time In the vast landscape of the digital world, criminal hacking has emerged as the foremost...
2 min read
Gleimi De Jesus : Mar 18, 2024 12:25:00 PM
In the fast-paced realm of cybersecurity, the simplicity of awareness often holds the key to robust defense. Individuals possess diverse learning styles, ranging from those who grasp instructions effortlessly with a single reading to those who thrive on visual or hands-on learning experiences. Recognizing and embracing these differences is at the core of effective cybersecurity training.
Learn more about our training program today and turn awareness into a powerful tool for your business's security! For a condensed version of this article click on our one pager below.
In today's cybersecurity landscape, it's noteworthy that cyber insurance increasingly requires organizations to undergo cybersecurity awareness training. Demonstrating a commitment to proactive defense not only safeguards your business but also aligns with the criteria set by cyber insurance providers.
As we navigate the digital landscape, it becomes evident that human error remains the leading cause of security breaches. Your team, undoubtedly your greatest asset, also poses the primary risk to your company's security. It's imperative to address this vulnerability with the right kind of cybersecurity training.
Breach Secure Now, commitment lies in providing continuous and interactive training. Why? The ever-evolving tactics of cybercriminals demand an adaptive and ongoing learning approach. This philosophy rejects the notion of a one-and-done mentality. Cybercrimes morph alongside our evolving lifestyles and work habits, making it crucial for us to stay ahead of potential risks.
Cybercriminals are opportunistic, ready to exploit emerging devices, capitalize on trending news, or take advantage of global events like pandemics. Their aim is to catch you off guard – whether for financial gain, identity theft, or orchestrating a subtle infiltration into your business that may go unnoticed for months. In this dynamic landscape, awareness becomes your first line of defense.
Breach Secure Now training approach seamlessly integrates different learning styles, catering not only to various individual preferences but also addressing the multitude of ways businesses can be targeted. The simplicity lies in recognizing that a holistic strategy is necessary, one that embraces diversity in learning habits to create a comprehensive shield against cyber threats.
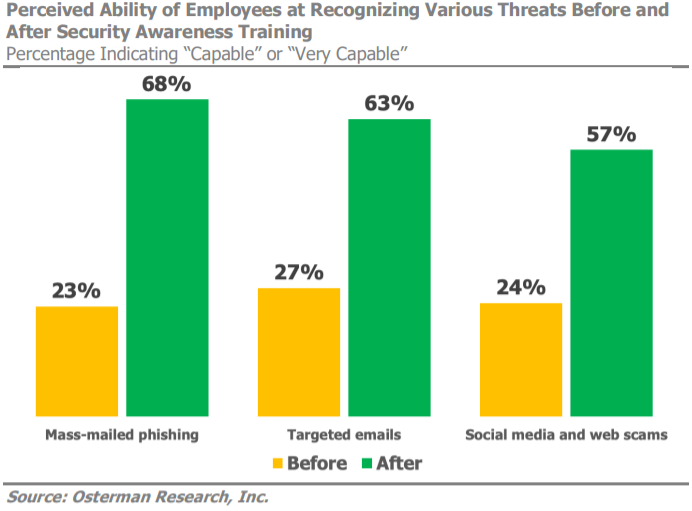
Whether you're an existing partner looking to maximize our tools and resources or a new acquaintance keen on safeguarding your clients' businesses, our award-winning training program is designed for you. Explore how integrated learning habits can enhance your cybersecurity posture and empower your team to navigate the evolving landscape with confidence. In a world where simplicity meets efficacy, awareness emerges as the cornerstone of cybersecurity resilience. Join us on the journey to fortify your defenses through the simplicity of the power of awareness and compliance.

2 min read
Navigating the Cyber Battlefield in the beginning of time In the vast landscape of the digital world, criminal hacking has emerged as the foremost...

Boost Your Business: Cybersecurity Training Spotlight In today's digital landscape, companies conduct the majority, if not all, of their operations...

The Importance of Security Risk Assessments As cybersecurity threats grow, businesses must stay ahead. Explore the significance of integrating...