Strengthen Your Data Security with Multi-Factor Authentication (MFA)
Introduction: In today's digital age, the protection of data and networks from cyber threats is paramount for organizations of all sizes....
2 min read
Ray Bidini
:
Oct 19, 2023 4:27:06 PM

In today's hyper-connected digital world, where the specter of cyber threats looms larger than everMulti-Factor Authentication (MFA) has emerged as a formidable weapon in the arsenal of cybersecurity. With hackers continually devising new tactics to infiltrate systems, MFA stands as an indispensable safeguard that can significantly reduce the risk of unauthorized access and data breaches.
The Multi-Layered Defense of MFA
At its core, MFA is distinguished by its multi-layered approach, setting it apart from the traditional username and password combination. This approach involves combining multiple factors of authentication, including something you know (like a password), something you have (such as a mobile device or security token), and something you are (biometric data like fingerprints or facial recognition). This dynamic combination creates a robust barrier that fortifies data security and poses a formidable challenge for hackers attempting to bypass authentication measures.
The Impressive Track Record of MFA
The statistics speak volumes about the effectiveness of MFA in the battle against password-based threats. Studies have revealed that MFA has an impressive success rate, blocking up to 99.9% of such threats. This figure is particularly significant in a world rife with data breaches and identity theft, where individuals and organizations alike must remain vigilant to protect their sensitive information.
The Critical Role of MFA Implementation
When implementing MFA, organizations must thoughtfully assess their options. A variety of methods are available, ranging from text messages and mobile apps to hardware tokens, each serving as a second factor of authentication. The choice of method depends on the unique needs of the business, taking into account factors such as user convenience, scalability, and compatibility with existing systems. Striking the right balance between security and usability ensures that MFA is a potent defense without becoming a cumbersome obstacle for users.
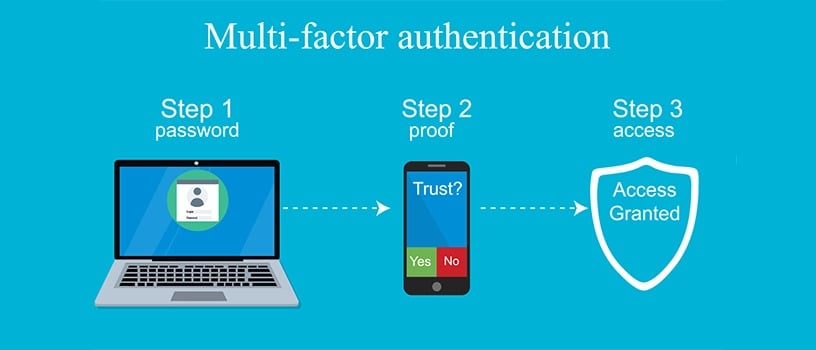
In the infographic above, the process works like this.
1. The person logs in with their username and password.
2. A second form of verification will be required (i.e. a confirmation message, pin, push notification, etc.) to access the account.
The relieving factor here with MFA is that if someone were to guess your password, they would have to bank on you providing them access by completing the second step such as clicking a link to grant access.
Empowering Users Through Education
Beyond the technical aspects of MFA, the education and empowerment of employees and users are pivotal. Providing comprehensive training and clear guidelines ensures that MFA is maximized for its security benefits. This includes educating users on common security risks, best practices for password management, and how to identify and report suspicious activities. An informed user base contributes to a proactive cybersecurity culture where everyone recognizes their role in maintaining a secure digital environment.
Embracing MFA: A Necessity for All Organizations
In conclusion, Multi-Factor Authentication has become a cornerstone of cybersecurity that no organization, regardless of its size, can afford to overlook. By demystifying MFA and deepening your understanding of its components and implementation strategies, you can bolster your organization's security posture and defend against the ever-evolving threat landscape.

Introduction: In today's digital age, the protection of data and networks from cyber threats is paramount for organizations of all sizes....

Strengthening Your Cybersecurity: The Role of SOC and Blackpoint Cyber In today’s ever-evolving cybersecurity landscape, businesses must take a...

If there’s one thing every business loves, it’s a solid return on investment (ROI). But when it comes to cybersecurity, many see it as an expense...