7 Simple Solutions to Secure your Business
In today's digitally driven world, protecting your business from cyber threats requires a comprehensive strategy. Gone are the days where installing...
2 min read
Ray Bidini
:
Oct 23, 2023 11:30:00 AM

In today's interconnected world, the importance of cybersecurity cannot be overstated. With the ever-evolving and sophisticated nature of cyber threats, it is absolutely crucial for businesses to prioritize the implementation of a robust cybersecurity training platform as part of their layered security approach. This blog post aims to provide you with a comprehensive guide on how to successfully implement such a platform within your organization.
Step 1: Understand Your Needs

Before delving into the process of setting up a cybersecurity training platform, it is imperative to have a clear understanding of your organization's specific needs. Take the time to identify your security goals and determine the types of threats that pose the greatest risk to your business. By doing so, you will be able to tailor your training program to effectively address these concerns. Check out our security awareness page that will help you understand what your business needs.
Step 2: Choose the Right Platform
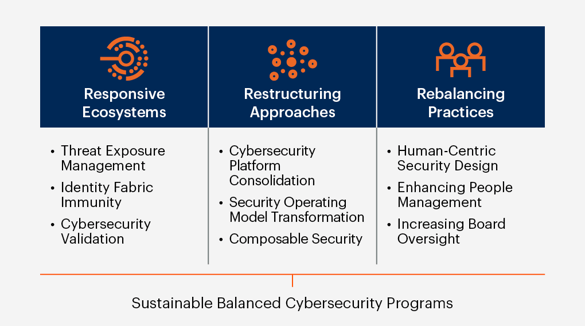
With a wide array of cybersecurity training platforms available, it is essential to carefully evaluate and select the one that best aligns with your requirements. Consider factors like user-friendliness, the breadth of training materials offered, and the platform's ability to simulate real-world cyber threats. Additionally, ensure that the platform adheres to the latest industry standards and stays updated with emerging cyber threats. Here are some different approaches that can be taken on deciding what cyber security platform would be best for your business.
Step 3: Set Up the Platform
Once you have chosen the ideal cybersecurity training platform, the next step is to configure it to suit your specific needs. This involves customizing the platform's settings, uploading relevant training materials, and creating user accounts for your employees. It is essential to ensure that the platform is easily accessible and user-friendly, allowing your employees to engage with the training materials seamlessly.
Step 4: Train Your Employees
With the platform fully set up, it is time to commence the training process for your employees. This can be achieved through a combination of online courses, interactive simulations, and quizzes. It is important to emphasize that the goal is not solely to educate your employees about cybersecurity but also to instill a behavioral change. Encourage active participation, foster a culture of vigilance, and provide practical tips and techniques that can be implemented in their daily work routines.
Step 5: Monitor Progress and Adjust as Necessary
The best part about these platforms is once they are set up they are extremely automated and require very little manual oversight to manage after the initial set up.
As your employees progress through the training program, it is crucial to monitor their development and make necessary adjustments along the way. Regularly assess their understanding of cybersecurity concepts, track their performance in simulations, and gather feedback to identify areas of improvement. This feedback loop will enable you to refine the training materials, introduce new content, and adapt the difficulty level of the simulations as required.
Conclusion - It's Easier than you think!
Implementing a cybersecurity training platform may seem like a daunting task, but with careful planning and execution, it can be a streamlined and efficient process. Remember, the benefits of having a well-trained workforce that can effectively protect against cyber threats are immeasurable. By investing in the development of your employees' cybersecurity skills, you are safeguarding your organization's sensitive data, reputation, and overall success in the digital landscape.
In today's digitally driven world, protecting your business from cyber threats requires a comprehensive strategy. Gone are the days where installing...

Boost Your Business: Cybersecurity Training Spotlight In today's digital landscape, companies conduct the majority, if not all, of their operations...
In today's hyper-connected digital world, where the specter of cyber threats looms larger than ever